
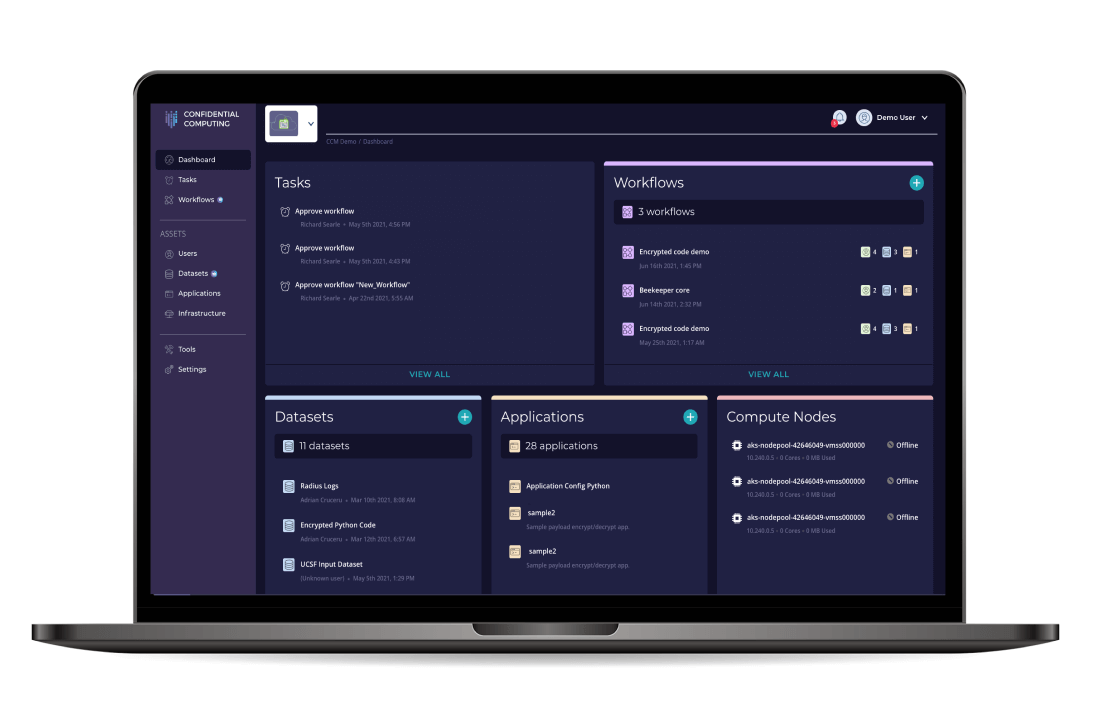
Overview
Data exists in three states: at rest, in use, and in transit. Data that is stored is "at rest", data that is being processed is "in use", and data that is traversing across the network is "in transit". Even if you encrypt data at rest and in transit across the network, the data they process are still vulnerable to unauthorized access and tampering at runtime. Protecting the data in use is critical to offer complete security across the data lifecycle. And in today’s data-driven world, it is best to rely on a method that focuses on the data itself.
Cryptography or encryption is now commonly used by organizations to protect data confidentiality (preventing unauthorized viewing) and data integrity (preventing unauthorized changes). There are now advanced data security platforms that enable applications to run within secure enclaves or trusted execution environments that offer encryption for the data and applications.
What is Confidential Computing?
Confidential computing is the protection of data in use using hardware-based Trusted Execution Environments (TEE). A Trusted Execution Environment is commonly defined as an environment that provides a level of assurance of data integrity, data confidentiality, and code integrity. A hardware-based TEE uses hardware-backed techniques to provide increased security guarantees for the execution of code and protection of data within that environment. (Confidential Computing Consortium)
How Confidential Computing Works?
Confidential computing protects data and applications by running them in secure enclaves that isolate the data and code to prevent unauthorized access, even when the compute infrastructure is compromised. Intel® SGX technology represents one of the leading implementations of Confidential Computing. Using Intel® SGX allows organizations to isolate the software and data from the underlying infrastructure (hardware or OS) by means of hardware-level encryption.
Implication: Organizations can now run sensitive applications and data on untrusted infrastructure, public clouds, and all other hosted environments. This gives organizations greater control over the security and privacy of applications and data inside and outside of their established security perimeter.
Benefits of Using Confidential Computing

Protect data and applications in use.

Secure intellectual property.

Enable secure encryption across the data lifecycle.

Prevent insider attacks and unauthorized access to data.

Get complete control over cloud data and seamlessly migrate/move workloads to the cloud.

Enable secure collaboration with external entities like partners and customers.
Use Cases
Secure and anonymous analytics on multiple data sets
Securing Healthcare AI
Secure Blockchain
Protecting data in use for ML models
Secure containerization
Protect Function-as-a-Service data
Fortanix Unlocks the Power of Confidential Computing
Fortanix has played a prominent role in taking Confidential Computing out of the lab and into the sunlight. Fortanix offers the most complete solution for confidential computing – providing customers the fastest and easiest path to protect their applications and data while in use.
Fortanix is a founding member of the Confidential Computing Consortium of the Linux Foundation. The Confidential Computing Consortium (CCC) brings together hardware vendors, cloud providers, and software developers to accelerate the adoption of Trusted Execution Environment (TEE) technologies and standards.

































 3910 Freedom Circle, Suite 104,
3910 Freedom Circle, Suite 104,