What is Intel® SGX?
Intel® Software Guard Extensions (Intel® SGX) technology provides a trusted execution environment (specifically, a secure “enclave”) for applications to operate in, securing the confidentiality and integrity of both the application and its data while the application is running.
This is achieved by encrypting the application and its data in system memory using an encryption key that never leaves the processor. The application and data are then decrypted on-the-fly inside the processor and any data written back out to memory is re-encrypted.
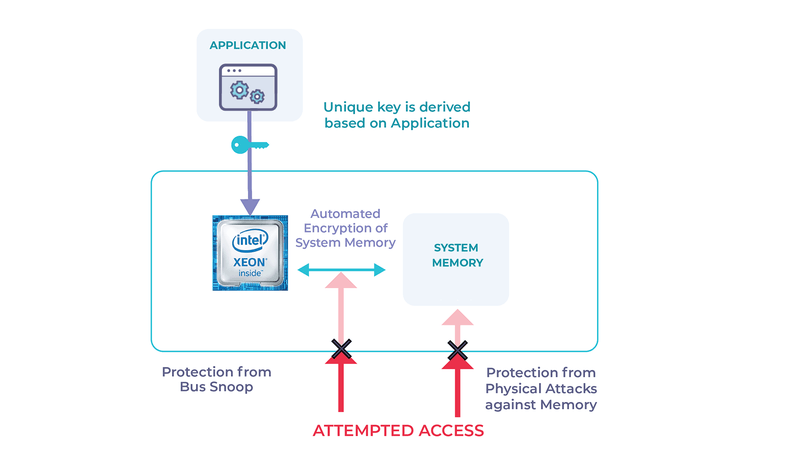
Since the encryption key is protected within the silicon, the only conventional ways to compromise the application or its data are (i) to brute force the key, which would take longer than the lifetime of the universe, even with every cloud computer in the world working on it, or (ii) to break the encryption algorithm, which has proven to be robust against all known attacks – not to mention that, if someone ever did manage to break AES, it would have very severe consequences for all encrypted data around the world.
Related Read: Five Things You Need to Know About Side Channels
What is the benefit of Intel® SGX?
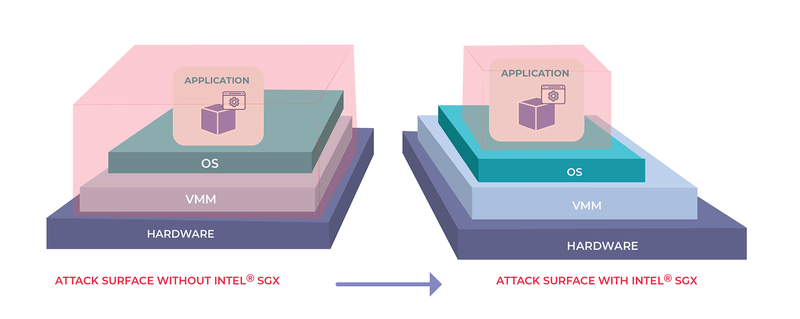
The benefit of Intel® SGX technology is that it reduces the trust boundary to just the processor and the application running within the secure enclave. Without Intel® SGX, the trust boundary includes all other applications in the system, the operating system, hypervisor, BIOS, server hardware, network infrastructure and system administration staff.
With Intel® SGX, you no longer need to trust any of these things – the confidentiality and integrity of applications and their data are protected against vulnerabilities in any of these components, including zero-day attacks that no anti-virus or firewall can stop, and no intrusion detection system (IDS) can detect.
Also read: How will Intel’s “Ice Lake” redefine the scope of data security?
No malware, malicious administrator or attacker gaining root privileges can compromise the data, even by physically probing the memory bus. Even side channel attacks on these components are rendered useless.
While standard encryption technologies protect data at rest and data in motion, Intel® SGX protects the final frontier - data in use. Thus, data breaches can become a thing of the past.
Processor side-channel attacks
However, remember that we still have to trust the processor. As processors have become more and more complex in an effort to enhance system performance, the scope for vulnerabilities in the processor itself has increased.
This fact first came to the world’s attention when the Meltdown and Spectre vulnerabilities were disclosed in 2017, which affected many processors from a number of vendors. These attacks exploited side-channels resulting from the complexity of modern processors – for example, features such as predictive branching.
Also read: More upcoming Intel SGX features explained
While Intel® SGX protects against some such attacks, it does not unfortunately protect against them all.

So, does this negate the benefits of Intel® SGX? Not at all! It should be remembered that an application is far better off using Intel® SGX than not using it.
The use of Intel® SGX technology protects against an enormous range of attack vectors, including many processors side-channel attacks, but there are still a few processors side-channel attacks that have nonetheless been shown to be effective even against Intel® SGX, and new attacks are still occasionally being found. However, all is not lost, as we shall see.
Firstly, side channel attacks are generally quite difficult to exploit in practice, relying on privileged access or very specific conditions, and require the attacker to first get a foothold on the target system in order to launch the attack.
At the RSA 2020 security conference in San Francisco, Intel announced that it patched a total of 11 CPU-related vulnerabilities in 2019, all of which were side-channel attacks that exploited the hardware architecture and internal design of Intel CPUs.
“These microarchitectural side-channel vulnerabilities are often closely related, generally difficult to exploit, and to Intel’s knowledge, have not been successfully utilized outside of a controlled lab environment at the time of this report,” the company said.
In 2019, 144 of the 236 CVEs (61%) published were discovered internally by Intel employees
Secondly, as part of its “Security First” pledge, Intel has focused on building an internal security team with some of the world’s top-tier security researchers, meant to find bugs before attackers, and tasked with uncovering bugs in the company’s products before they reach store shelves.
“In 2019, 144 of the 236 CVEs (61%) published were discovered internally by Intel employees,” the company said. “We believe documenting and publicizing internally found vulnerabilities provides a critical level of transparency to our customers.”
In response to the vulnerabilities that have been discovered, Intel has issued microcode updates, incorporated silicon-level fixes into new CPUs, and recommended software developers employ mitigations where appropriate, such as disabling certain advanced CPU features like hyperthreading or flushing caches at critical points in the code path.
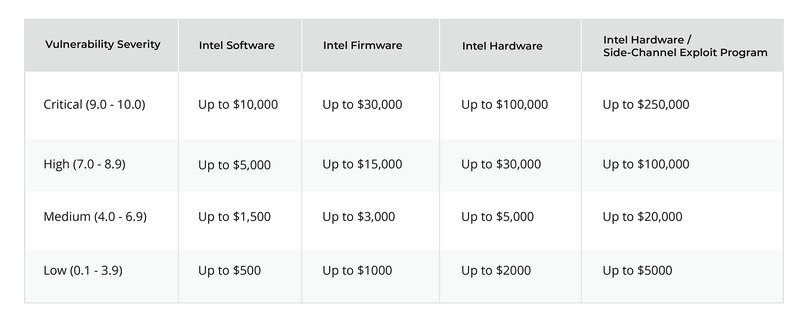
Intel also offers a bug bounty to encourage researchers to find and responsibly disclose new side channel vulnerabilities. This bug bounty is intended to flush out vulnerabilities as quickly as possible and has generated a predictable wave of new vulnerability disclosures as researchers' cash-in on the potential rewards.
This pro-active approach to security enhancement enables Intel and its partners, such as Fortanix, to implement and roll-out fixes before the vulnerabilities are publicly disclosed.
Unfortunately, the technical press tends to exaggerate the impact of many of these vulnerabilities and they are rarely discussed in the context of a security model without the protection provided by Intel® SGX.
Researchers have also been known to make bold statements about the impact of their findings on Intel® SGX, as this technology is perceived as Intel’s crown jewels and there is much kudos in finding a chink in its armor.
Furthermore, it should be noted that the SGX architecture itself has never been broken – all the published attacks against SGX have rather been related to the underlying micro-architecture of the CPU.
For more information, download the Side Channel and Runtime Encryption Solutions with Intel® SGX whitepaper.
Conclusion
In reality, not all new side-channel attacks impact Intel® SGX, and many of those that do are already addressed by previous fixes or mitigations. Where new vulnerabilities are exposed, Intel works quickly to fix them before they are disclosed.
As the leader in commercial applications that leverage Intel® SGX, Fortanix routinely implements all necessary fixes and mitigations, employing many cryptographic specialists to oversee the work (including one of the authors of the Foreshadow vulnerability paper).
On top of this, Fortanix employs many other (more traditional) security measures, up to and including hardware tamper detection and response, to provide defense in depth with security certification up to FIPS 140-2 Level 3.
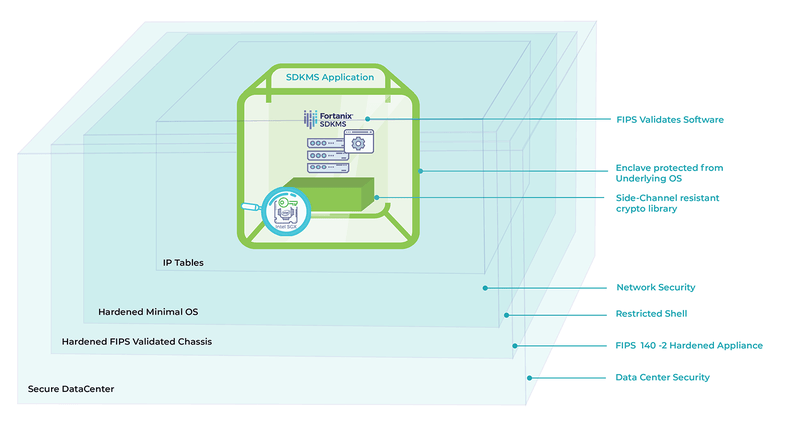
This enables us to ensure that Fortanix Runtime Encryption® products based on Intel® SGX technology, including our Fortanix DSM, which re-defines the concept of a hardware security module (HSM), continue to provide the best security on the market.
For more information, download the Fortanix DSM with Intel Sofware Guard Extensions (Intel® SGX) whitepaper.











