Companies are increasingly opting for cloud infrastructure as it offers easy deployment, scalability, minimizes operations costs, and accelerates innovation. However, an ineffective multi-cloud security strategy can risk data protection and privacy.
Attackers can breach data in a multi-cloud environment because of misconfiguration, poor encryption, flawed key management, insufficient credential management, and insecure API. As a result, cloud data protection has become a prime concern.
Secondly, consumers’ anxiety over data privacy has pushed companies to abide by the data protection protocols. For instance, according to a research study conducted by KPMG, 86% of the respondents feel a growing concern about data privacy, while 78% expressed fears about collecting data.
In addition, according to the EY Global Consumer Privacy Survey, 63% of consumers want to know how organizations collect, store and secure their personal data. The statistics published in these reports further explain why companies need to prioritize data security.
However, it is challenging to apply a unified framework for data control, access, and security policies across multiple clouds.
Every cloud provider has a different approach/mechanism to manage cloud data and keys, leading to the inconsistent management of data and keys across multi-cloud.
Additionally, with cloud keys under the control of the CSP, there is an increasing probability of cloud insider threats, and it’s complex to meet compliance regulations. As a result, workflows operating on different clouds mean companies lack visibility into data and security loopholes.
Cloud service providers (CSPs) are primarily responsible for the security and the seamless delivery of their services; however, companies are solely responsible for data security in a multicloud environment.
Here’s what you can do to establish a robust multi cloud data security setup.
1. Centralize Policy Configuration from Single Console
CSPs offer encryption, usage, and policy configuration, but the problem is that there is a different approach/systems/tools for each cloud. If your data is in multicloud, configuring uniform policies across clouds is complex and requires manual configuration.
For example, with stringent privacy regulations like HIPAA, healthcare providers often need to create specific policies to control data access. If the data is spread across different cloud providers, applying a uniform framework for access and control becomes complex and time-consuming.
As a solution, ensure a Key Management System (with capabilities like BYOK) that can connect to each of these clouds and set consistent policies across cloud environments from one single console.
2. Integrate Security into DevOps
Cybercriminals have become proficient at accessing cryptographic keys, tokens, passwords that developers often leave behind on applications, sites, and files. This is why DevOps and Security teams cannot work in silos, and there is a need for shared responsibility in managing innovation and security together.
Developers can work using data security interfaces. The collaboration between two teams will help implement efficient secrets management, integrate crypto into applications in the coding phase, and substitute a token for sensitive data using a REST API.
3. Integrate Data Security Capabilities as a SaaS
SaaS products are vastly scalable and match the agility of your cloud infrastructures. In addition, they streamline automation across different applications and locations and improve overall efficiency.
The SaaS-based data security model is easier to integrate with apps, IT infrastructure, services and requires no specialized skills for deployment. It includes simplified operations with zero management overhead/ hardware. You can start with a small setup and scale up as business operations expand.
Moreover, you’ll benefit more from a solution that offers all possible capabilities from a single platform that secures data wherever it resides and across the data lifecycle, including Encryption, Key Management, Tokenization, Secrets Management, etc.
4. Manage a Single Dashboard
A single window dashboard helps you govern and audit the entire multi-cloud data environment/Infrastructure. For example, you can check the encryption status of endpoints and Virtual Machines (VM) across multicloud environments from a single screen.
In addition, it is best to have a Key Management System that integrates with a SIEM tool like Splunk providing for event log analysis and correlation.
As a result, you can assess all users across various locations accessing the data and its impact on business operations. Further, you can track all user activities in your network, get alerts, identify and respond to security threats.
As you do not have to review complex data stacks across hybrid infrastructure, a single dashboard saves time and minimizes operational costs.

5. Deploy Zero Trust Data Protection
Do not trust but verify. A zero-trust architecture (ZTA) ensures that you give access to only those authorized users to manage a particular data set. In addition, you can microsegment the permissions granted for data access.
For example, user authentication factors can include multiple verifications such as validating name, password, biometrics, device type, software, location, and time.
Once users access data, they must further validate their credentials to process the data for downloading, editing, or transferring it across multiple folders.
In addition, enforce application-level policies, which means only authorized applications can be allowed to process the data.
The success of zero-trust architecture is higher when you consider a sole vendor that has a full-stack solution because multiple point solutions increase integration challenges and management considerations.
6. Own the Master Key
Bring Your Own Key (BYOK) is one of the most secure ways to protect your cloud data. Here you bring or import your own master key, which the cloud provider stores in their key management system (KMS).
The cloud KMS protects the data encryption keys (DEKs) by using your master key before it stores the data. If you delete this key to stop a progressing breach, you can always import the same key back into the cloud KMS later to reclaim your data. In addition, you have a copy of the master key in case of loss of the key.
However, to avoid management complexities, you can ensure the master keys are always securely stored in your off-cloud Key Management System. As a result, the cloud provider never gets access to your master key.
In addition, you can revoke access to the master key anytime, making data immediately inaccessible by any application or service. Connect with our team to know more.

7. Secure Data with Confidential Computing
You can be confident that your data protection policies protect your data only when you encrypt data at rest, in motion, and in use. Often, companies face data encryption challenges because data is encrypted at rest and in transit, but it is rarely encrypted while in use by applications.
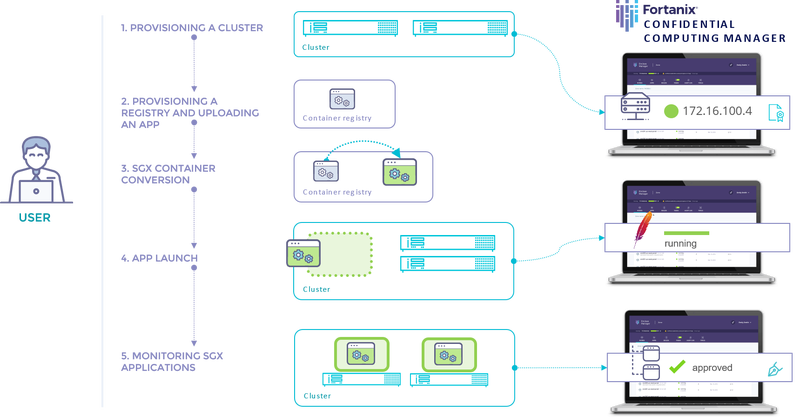
Confidential Computing makes it possible to secure data in use. Promoted by the Confidential Computing Consortium, Confidential Computing is a concept that uses hardware-based trusted execution environments (TEEs) called enclaves.
It isolates and secures the CPU and memory used by the code and data from potentially compromised software, operating systems, or other VMs (Virtual Machines) running on the same server.
There are two distinct approaches to implementing Confidential Computing technology: developing or rewriting applications and a plug-and-play conversion of the application.
Learn how these two approaches solve the challenge of keeping confidential data and proprietary algorithms secure.
A data security strategy in cloud environment requires a continuous and consistent assessment to ensure real-time data protection, advanced standards alignment, and compliance with all regulatory laws.
Companies can benefit from designing and implementing a unified data security strategy that help them manage the data deployed in the cloud, data encryption; and control the master keys.










