There are ample chances that your team members already rely on Google workspace in one way or another. It could be Gmail for business, Google Duo for video calls, or Google Drive for sharing documents and presentations with peers. Seemingly everyone knows about Google Workspace: schools, colleges, businesses, government offices, enterprises, grandparents, and neighbors.
The idea of a cloud-based productivity suite was a rarity in the industry, back when software needed physical installation and files could only be shared via flash drives. Today Google Workspace clocks more than 6 million active accounts worldwide—empowering digitization for countless businesses and exploring the ability to work in new ways.
It broke traditional conventions around collaborative activities by mitigating the notion that such tasks required closed board rooms—ticking all the checkboxes on businesses’ productivity and communication checklist.
The Security Piece
All this data coursing through the Google platform is sensitive and mission-critical—making data encryption an indispensable part of the Google Workspace security strategy.
To that note, the data that traverses through GCP is first encrypted while at rest — sitting on a disk (including solid-state drives) or backup media. If a breach occurs, the attacker simply fails to decipher the data without the necessary encryption key—even if they have access to the storage equipment holding your data.
Google also encrypts the user data while in transit. If an attacker tries to intercept data running over the internet and across the Google data centers—he gets nothing but scrambled data that can only be deciphered by the users in possession of the secret key.
The importance of creating, managing, and securing these keys is hardly debatable.
Key Management and Decryption Process
Strong data encryption is built upon the holy grail of stronger key management. Google boasts a robust proprietary service to facilitate the management, distribution, generation, rotation, and management of cryptographic keys using industry-standard cryptographic algorithms that obey industries’ best security practices.
But wait. There’s more to it.
Google Workspace Client-Side Encryption
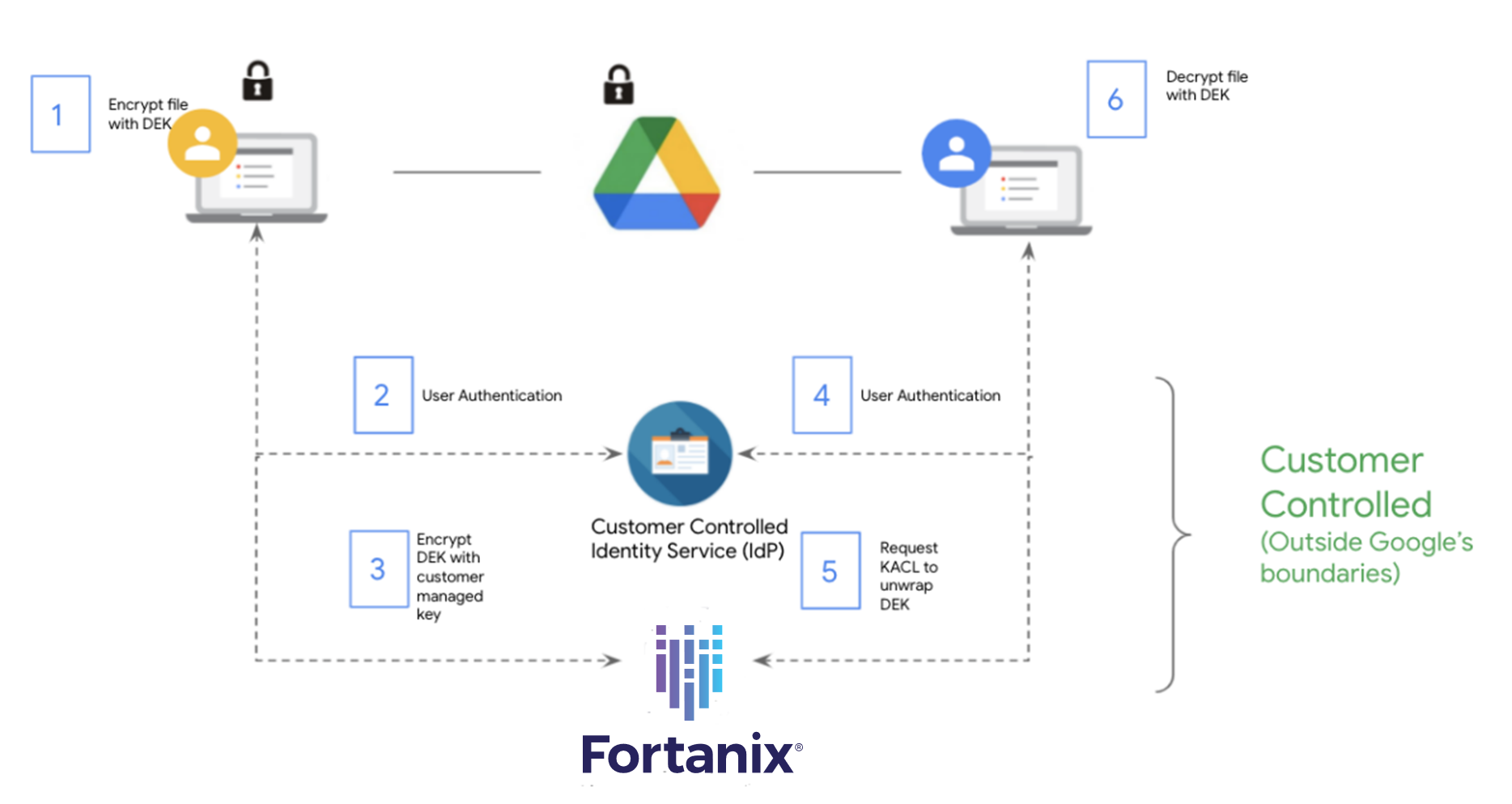
Traditionally, when encrypting data at rest and in transit, the cryptographic keys rest with Google. But, given that certain customers want more granular control over their data, Google now has Client-side encryption — giving customers direct control of encryption keys, thereby making customer data indecipherable to Google. This security feature gives Google’s enterprise customers direct control of their encryption keys and the identity service they select to access the keys.
Tell Me More
Google CSE takes a momentous leap towards helping customers meet data sovereignty and compliance needs with zero impact on end-user experience. The product is built around the following principles:
-
Complete control over encryption keys: For leveraging Google CSE users need to need to set up their encryption key access service with an external key manager that abides to CSE requirement.
-
No access to plain-text content: Your Google Workspace data gets encrypted in the browser before taking off to the Google servers. If Google needs access to this data, it will need explicit customer authorization on a per-file basis.
-
Minimized impact on user experience: This feature in no way intrudes or alters the end-user experience. It’s important to note that CSE targets file content for this additional layer of encryption. Most of the metadata, including file names, labels, and the access control list, continue to be available to Google for running the service.
Using Client-side encryption is optional for eligible Google Workspace customers, who can deploy CSE to their entire organization or a select set of users within their organization.

Fortanix and Google CSE: Stronger Privacy and Better Data Security
Fortanix Data Security Manager integrates with Google Workspace External CSE to replicate the same level of security for the keys as in an on-premises environment while moving their data to the cloud. Not only is the data undecipherable to Google, but the encryption keys are also never stored in GCP. The user has complete control over the authorization of Google Workplace data and keys.
Users also get to define and control policies for Google Workspace Key Encryption Key (KEK) from Fortanix DSM SaaS account. Upon receiving the file, the corresponding data encryption key is decrypted using customer-provided keys only after authenticating the user with customer-controlled authentication.
Fortanix DSM SaaS provides FIPS 140-2 Level 3 hardware-based protection, with complete separation between users and regions as needed. It also offers centralized management with audit logging, enterprise-level access controls, multisite and hybrid cloud support, built-in encryption, key management, tokenization, and support for various interfaces, including REST APIs, PKCS11, CNG JCE, and KMIP.
Conclusion
Data, unlike other forms of personal assets, is simply more…complicated. Google CSE aims at creating a mechanism that gives users more control—particularly useful for businesses that run atop sensitive or regulated data. Think healthcare records, financial data, and similar intellectual property.
We understand that many of you will need help in this area to get it right from the get-go, and Fortanix is here to help you build this capability.
“Through our partnership with Google Workspace Client-side encryption, Fortanix is offering FIPS 140-2 Level 3 hardware-based protection, with complete separation between users and regions as needed, and many more security features to protect your Google Workspace keys and data — on the go, on any device, anywhere in the world.” said Ambuj Kumar, ex CEO and co-founder of Fortanix.
Fortanix is hosting a webinar that dives deep into Google Workspace security best practices and the value and mobility that Fortanix DSM SaaS brings to the table.
Want a personalized solution for your data security woes? Talk to our experts.










