Saturday Night Fever
The 1970s disco era saw the invention of floppy disks, home video cassette recorders (VCRs), Atari games consoles, the first Apple PC, the Sony Walkman, and many other gadgets. All great inventions but now found only in museums or the hands of memorabilia collectors.

The 1970s also saw the birth of the Hardware Security Module (HSM) – a dedicated hardware device for generating, storing, and processing cryptographic keys, developed originally to process electronic payment transactions.
HSMs are “So Last Century”!
Somehow, the HSM appears to have miraculously stood the test of time and is still used today – it has barely evolved though. Yes, HSMs have gotten faster and now support a wider range of cryptographic algorithms and operations, but architecturally they are still basically the same – a proprietary black box with some magic inside and an arcane API.
Yet, they are widely used in a myriad of security systems where strong security is paramount, such as public key infrastructures and key management systems.
Is the HSM concept really so good that it can’t be improved upon? Or is there simply not enough competition to drive meaningful innovation? Actually, both. The intrinsic security of HSMs comes from the immutability of their hardware, which is generally less susceptible to hacking than software, but heavily constrains their architecture.
Also, the complexity and cost of developing and certifying a new HSM, not to mention the challenge of overcoming customers’ conservatism towards tried-and-tested brands, creates a significant barrier to entry for new vendors, which has resulted in the market being dominated by a handful of vendors with little incentive to innovate.
As a result, we are stuck with hardware bricks that need to be ripped out and replaced every few years, require a PhD to install and operate, and involve mystical key ceremonies where a group of people huddle around a worshipped HSM to give offerings of smart cards (not exactly COVID-safe!).
Moreover, they simply don’t provide the scalability, resilience, upgradeability, or DevOps-friendliness that today’s generation of security architects, educated in a cloud-first IT world, expect and need.
Is There an Alternative?
In the past, the only way to build a secure hardware product was to design it from the ground up, but today there are many off-the-shelf hardware security components and technologies to save you the hassle.
Trusted Platform Modules (TPMs) were arguably the first generation of off-the-shelf hardware security components, albeit limited in capability, and these were followed by processor manufacturers building better security into their standard CPUs.
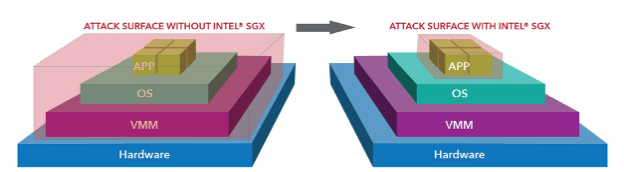
Description automatically generated, for example, Intel® Software Guard Extensions (SGX) provides a Trusted Execution Environment (TEE) that allows applications to run within a secure enclave with hardware-enforced isolation and protection of code and data in system memory (using encryption).
This means that software applications can now be built and operated in a public/private cloud environment with similar security characteristics to dedicated hardware devices like HSMs.
Related Read: Pioneers, HSMs, and the Future
Check out our infographic on HSM is Dead Long Live HSM
Introducing Fortanix Data Security Manager (DSM)
Fortanix has leveraged Intel® SGX technology to disrupt the HSM market and create a virtual HSM that can be deployed in virtual environments, public clouds, or even (to keep HSM loyalists happy) a physical hardware appliance. This new architectural approach to designing an HSM has many far-reaching benefits:
-
Freedom to employ the latest cloud-native software technologies, enabling active-active clustering for unlimited scalability and mission-critical availability.
-
Ease of incorporating additional security components within the same product (e.g., key management system, secrets management, tokenization), all managed through a single- pane-of-glass – no need to buy and manage multiple, loosely-integrated products.
-
Fully API-driven architecture, enabling automation and use within CI/CD pipelines.
-
Unlimited functional upgrades without requiring hardware changes, applied easily and without downtime.
-
100% remotely managed, no physical access required during operation.
-
Unlimited multi-tenancy capability, enabling a truly elastic SaaS model.
-
Ability to run custom scripts within secure enclaves to extend product functionality for bespoke integrations and business logic.
-
Licenses are not tied to a specific hardware device, but can be freely migrated between appliances (either physical or virtual)
Don’t Buy an HSM
This leaves you with zero incentives to buy an HSM.
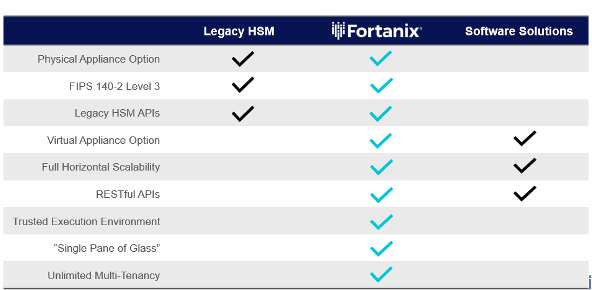
Instead, Fortanix DSM delivers all the benefits of a traditional HSM (including certification up to FIPS 140-2 Level 3 on the optional hardware appliance) along with all the benefits of a software-based security solution, plus many new and unique capabilities, all built into an integrated data security platform available as a virtual/physical appliance or SaaS service.
Our solution is trusted by the likes of PayPal, Standard Chartered Bank, Adidas, and numerous Fortune Global 500 companies. Request a demo now.

 Cite this article
Cite this article








