Customer Profile
Goldman Sachs is an American multinational investment bank and financial services company. Founded in 1869, Goldman Sachs is headquartered at 200 West Street in Lower Manhattan, with regional headquarters in London, Warsaw, Bangalore, Hong Kong, Tokyo, Dallas and Salt Lake City, and additional offices in other international financial centers. Goldman Sachs is the second largest investment bank in the world by revenue and is ranked 57th on the Fortune 500 list of the largest United States corporations by total revenue.
USE CASE
ComplianceINDUSTRY
Financial servicesPRODUCTS

Business Challenge:

Business Challenge:
- Goldman Sachs was looking to increase efficiency and manage expenses around backup media and the operational needs of managing the backups. Moving the various structured and unstructured data in the scattered on-premises Hadoop data lakes toward a centralized Amazon S3 environment enables more flexibility in accessing this data when required.
- However, migrating these data lakes required a robust encryption implementation to comply with data privacy and security regulations. With strong encryption mechanisms and key ownership, Goldman Sachs maintains control of their data and enforces segregation of data and keys.
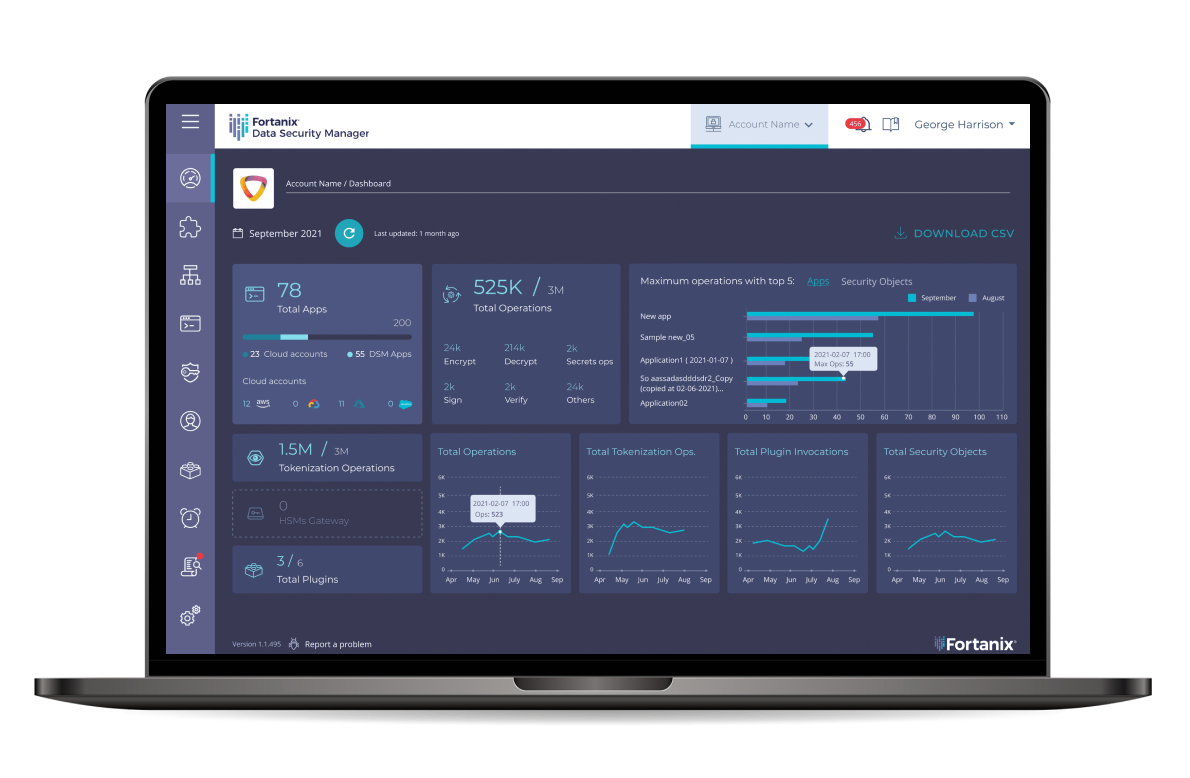
Solutions
- To ensure the keys stay segregated from where the data is stored and to provide the IT security team complete control of all keys and their lifecycles, Goldman Sachs needed to encrypt the data before uploading it to AWS S3. Therefore, Goldman Sachs first integrated Fortanix’s encryption workflows into the Hadoop environment to generate and securely transport Data Encryption Keys (DEKs), which in turn are protected by Key Encryption Keys, stored on FIPS 140-2 Level 3 validated HSMs. This way, access to files and data blocks is fully controlled by Fortanix DSM with granular role-based access policies.
- With Fortanix DSM, the teams automated the key rotation process to simplify their operations, including regenerating keys when S3 objects are overwritten. Fortanix DSM’s Quorum Control feature also requires the approval of multiple administrators for sensitive key operations such as deleting a key. Regardless of the volume of data stored, Key Management operations are now very easy; managing keys to encrypt and decrypt takes just a couple of clicks.
- Goldman Sachs also built a strong relationship with the Fortanix sales teams to evaluate and deploy use cases, knowing they have stellar support whenever it’s required.
Featured Products
Expand digital experiences in Europe
Fortanix and Goldman Sachs also collaborated to extend their global state-of-the-art platform to an expanded European client base, exposing them to the same digital experience that other clients worldwide enjoy. In Europe it is key to ensure that the global platform meets all local regulatory requirements, which can create complex access management and encryption requirements. Therefore, this required a very advanced key management solution to help expedite the rollout in a controlled fashion.
Key requirements included granular access control while maintaining simplified deployment and operations. After diligent efforts to evaluate different vendor solutions, the Fortanix Data Security Manager (DSM) platform was selected to meet the needs of the Goldman Sachs team.
The usability of Fortanix DSM was also a key factor: it provides an intuitive user interface that their application and security teams found easy to use in their workflows. The fact that users could start encryption or decryption operations without seeing the encryption key was considered a benefit. Deploying Fortanix DSM was a smooth experience; the teams had the ability to set up the cluster with fail-safe mechanisms such as Disaster Recovery (DR) and High Availability (HA) without effort.
Why Goldman Sachs Chose Fortanix?

Ease of deployment, integration, and management

Key Sovereignty














 3910 Freedom Circle, Suite 104,
3910 Freedom Circle, Suite 104,