Power the Way to a Quantum-Safe Future.
Post-Quantum Cryptography transition is not an algorithm switch. It is a long and strategic journey that needs to start today.

Overview
Quantum computers are advancing rapidly, threatening traditional cryptographic methods like RSA and ECC, which can be broken by quantum algorithms such as Shor’s. This puts sensitive, long-term data at risk as adversaries collect encrypted information to decrypt later.
Transitioning to Post-Quantum Cryptography (PQC) is a strategic shift not just a code update. It requires assessing current cryptography, updating systems, and preparing people and processes. Don’t delay the transition start the journey to PQC transition today to avoid crisis response tomorrow.
Accelerate Post-Quantum Readiness with Fortanix
The Fortanix unified data security platform transforms PQC complexity into actionable insights, strategic priorities, and streamlined operations. With visibility into cryptographic assets, guided roadmap, and disruption-free migration, you now can accelerate readiness, reduce risk and cost, and confidently navigate the journey with clear objectives and control.

Assess Readiness
Identify quantum-vulnerable assets, quantify impact, and drive alignment around real risk.

Prioritize Roadmap
Prioritize exposure, balance short- and long-term wins, and automate the backlog resolution.

Streamline Transition
Test readiness, centrally track progress, and continuously assess risk for disruption-free migration.
Start Your PQC Readiness Journey Now
PQC Central, a major feature of the Fortanix platform, reframes how enterprises approach the post-quantum cryptography challenge. It starts by answering a critical question: How exposed are you? With a prioritized list that can be used to develop a PQC migration roadmap and way to upgrade algorithms without hardware changes or operational disruptions, you now can easily begin your PQC transition. Fortanix is the industry’s only platform that facilitates end-to-end PQC readiness, and the four-step approach includes:
Discover
Begin by identifying quantum-vulnerable assets across your enterprise-wide systems.
- Map your entire cryptographic security posture.
- Inventory all encryption keys and data services across multi-cloud, multi-geography and on-premises environments.
- Get full visibility into key locations, statuses, and usage across critical data services.
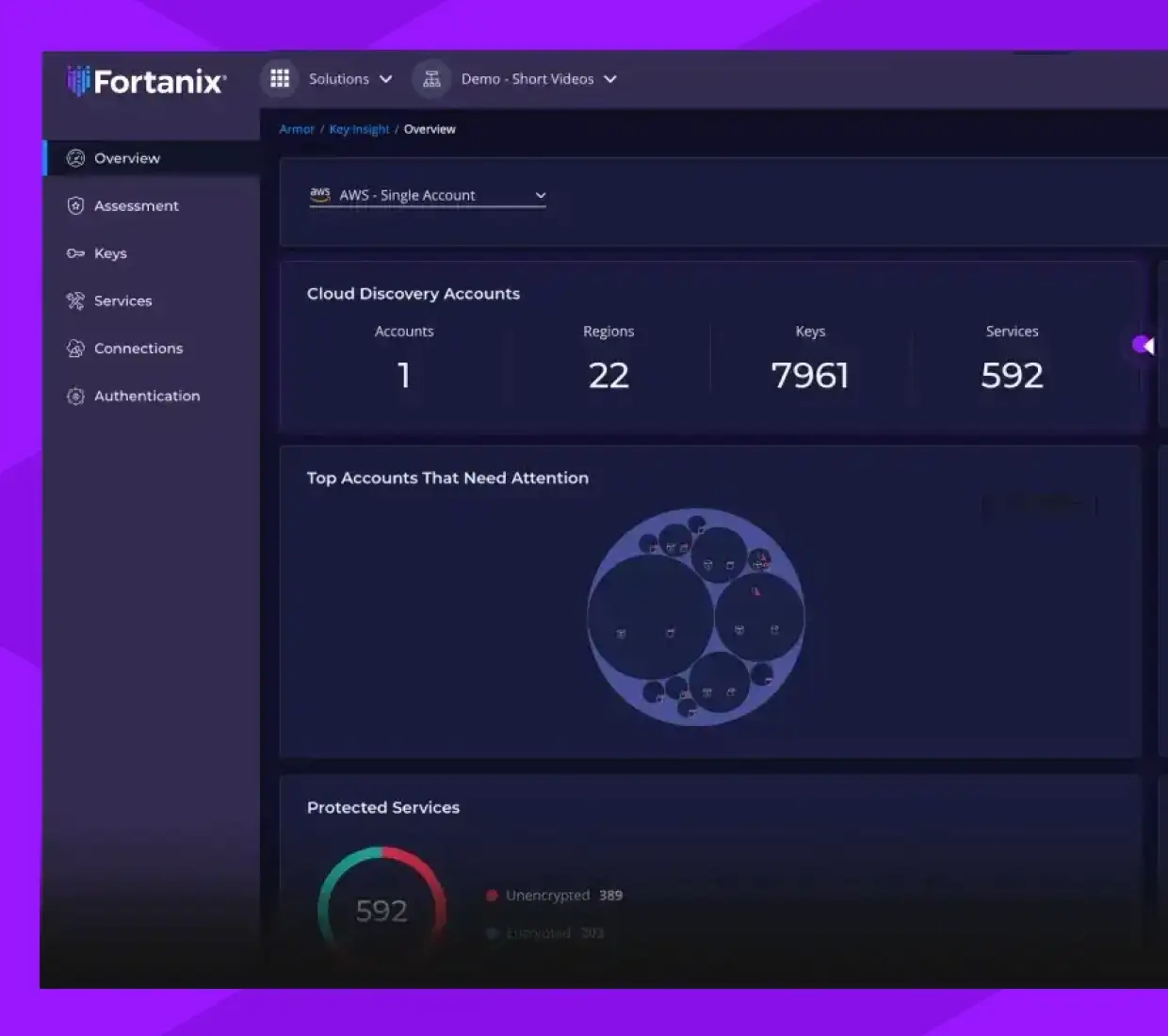
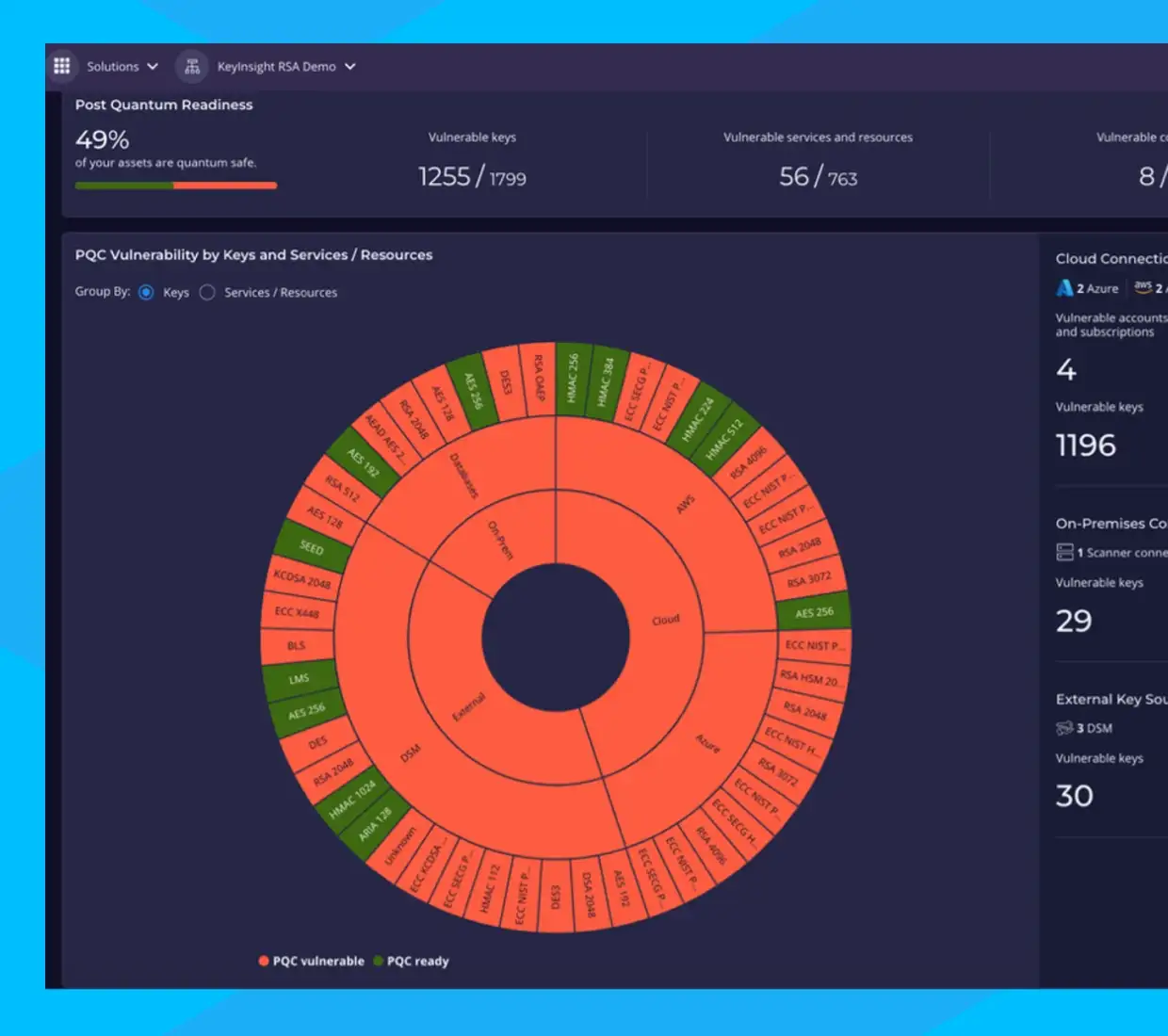
PQC Assessment
Understand vulnerabilities through an intuitive dashboard and heat maps to prioritize high-risk assets.
- Benchmark your cryptographic security posture against emerging post-quantum computing threats.
- Identify gaps and detect data services lacking proper encryption or protection.
- Benchmark your cryptographic security posture against emerging post-quantum computing threats.
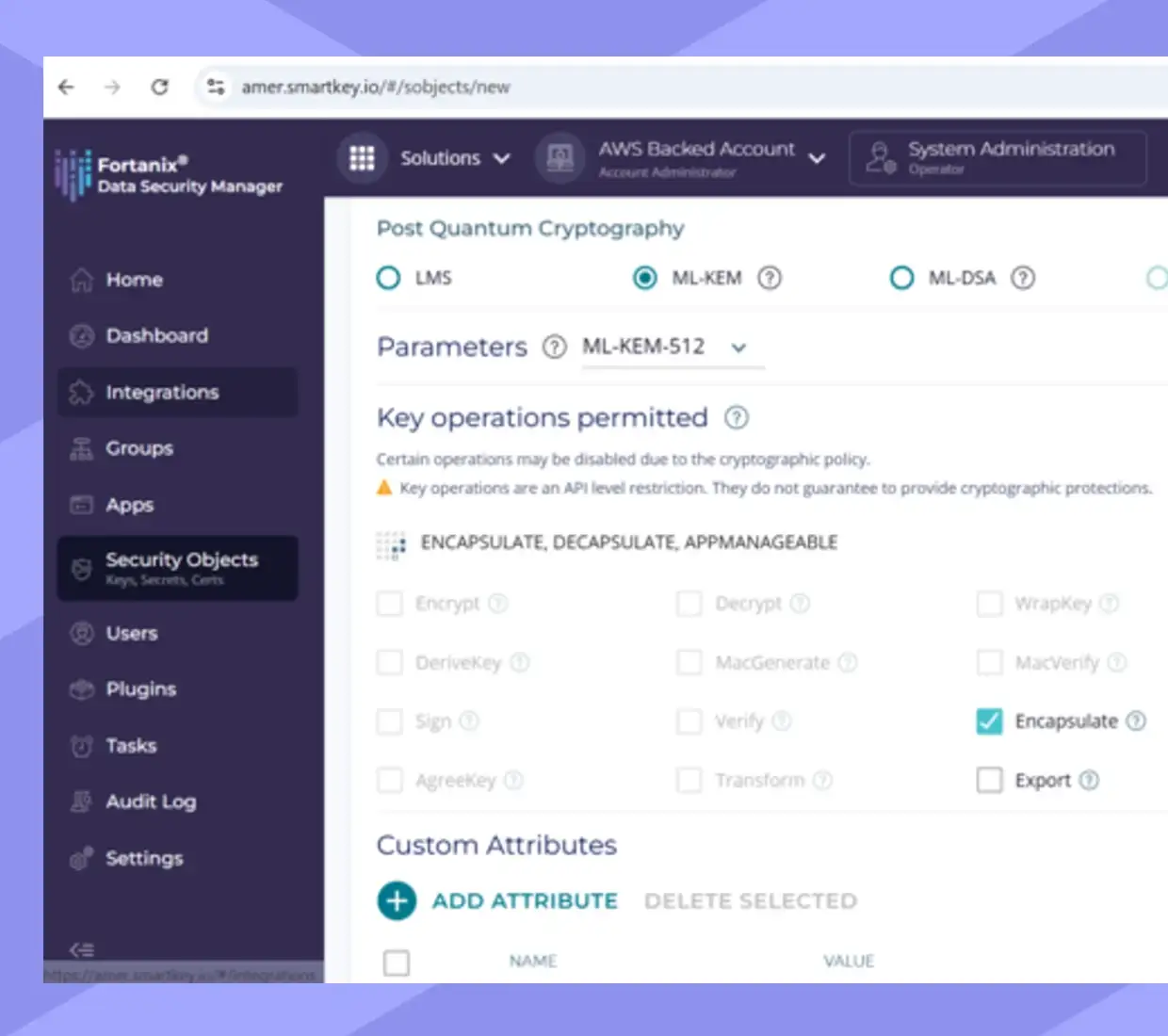
PQC Transition
Migrate to post-quantum cryptographic algorithms without disruption.
- Centrally manage all encryption keys and policies
- Enforce compliance and governance with the latest security standards, algorithms and policies.
- Test your readiness before deployment to prevent costly outages.
- Automate manual processes to eliminate human error, reduce inconsistencies, and enhance overall data security.
Crypto-agility
Continuously evaluate and be ready to adopt future cryptographic advancements.
- Consciously evaluate your PQC posture as you add new services and systems to migrate without disruption.
- Quickly adapt to a new cryptographic system without updating key management systems or HSM deployments.
Start Securing Against Quantum Threats Today
NIST released a set of Post-Quantum Cryptography (PQC) standards so organizations can upgrade their cryptographic footprint. Fortanix supports the full suite of algorithms in the Commercial National Security Algorithm Suite (CNSA) 2.0. Our platform is built for agility and will swiftly implement updates and new standards when they arise.
| Algorithm | Function | Specification | Parameters |
|---|---|---|---|
| Advanced Encryption Standard (AES) | Symmetric block cipher for information protection | FIPS PUB 197 | Use 256-bit keys for all classification levels. |
| CRYSTALS-Kyber (ML-KEM) | Asymmetric algorithm for key establishment | FIPS PUB 203 | Use Level V parameters for all classification levels. |
| CRYSTALS-Dilithium (ML-DSA) | Asymmetric algorithm for digital signatures | FIPS PUB 204 | Use Level V parameters for all classification levels. |
| Secure Hash Algorithm (SHA) | Secure Hash Algorithm (SHA) | FIPS PUB 180-4 | Use SHA-384 or SHA512 for all classification levels. |
| Leighton-Micali Signature (LMS) | Asymmetric algorithm for digitally signing firmware and software | NIST SP 800-208 | All parameters approved for all classification levels. SHA-256/192 recommended. |
| eXtended Merkle Signature Scheme (XMSS) | Asymmetric algorithm for digitally signing firmware and software | NIST SP 800-208 | All parameters approved for all classification levels. |
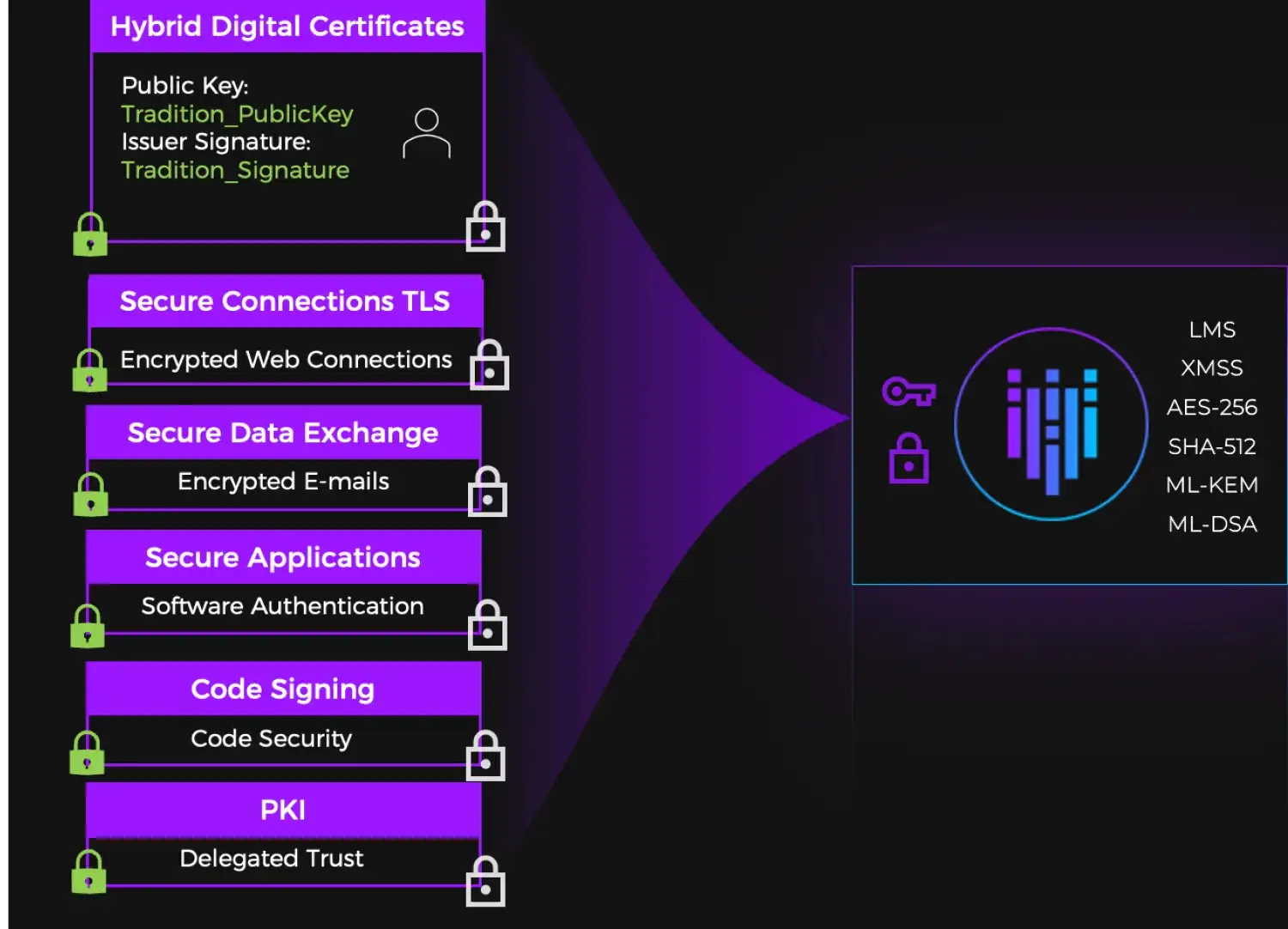
PQC Use Cases
Quantum vulnerabilities threaten core components of modern security, particularly where asymmetric cryptography is embedded-- public key infrastructure, user authentication flows, firmware signing, software delivery, and more. Current algorithms, like RSA and ECC, widely used for authentication and secure key exchange, need to be transitioned to quantum-safe alternatives now to safeguard against future compromise.
Trust Fortanix to help you plan your PQC journey, centralize encryption key management, and securely store keys in FIPS 140-2 Level 3 Hardware Security Modules (HSMs), available on-prem or as SaaS.
Featured Resources
Here are some of latest news, blogs, resources, events, and more






Press Release
Fortanix Enhances Data-First Security Platform to Secure Against Escalating AI and Quantum Computing Threats